SecurStar Encryption
Disk & Desktop Encryption Software
DRIVECRYPT securely and easily protects all proprietary data on notebooks and desktop
computers 100% of the time without users having to think about security. Any organization,
from a small company to a large international firm with thousands of users in the field, can
effectively protect business plans, client lists, product specifications, confidential corporate
memos, stock information, and much more with this disk encryption product.
With its Traveller modus functionality, DriveCrypt is the ideal solution to encrypt
USB disks and Pen drives without needing to install the software on the computer
DriveCrypt 1344 Bit Disk Encryption
|
As data is read from the hard disk, DRIVECRYPT automatically decrypts the data before it
is loaded into memory. When data is written back to the hard disk, it is automatically reencrypted.
The disk encryption/ decryption process is completely transparent to the user or
any application program -the data is caught "on the fly" as it transfers back and forth
between the hard disk and memory. Consequently, users don't need to remember to
decrypt or re-encrypt their data, or change the normal operation of the PC. In addition, only
individual files are decrypted at any one time, not the whole hard disk.
How DriveCrypt`s On-the-fly Encryption Works
As data is read from the hard disk, DRIVECRYPT automatically decrypts the data before it is loaded into memory. When data is written back to the hard disk, it is automatically re-encrypted. The disk encryption/ decryption process is completely transparent to the user or any application program -the data is caught "on the fly" as it transfers back and forth between the hard disk and memory. Consequently, users don't need to remember to decrypt or re-encrypt their data, or change the normal operation of the PC. In addition, only individual files are decrypted at any one time, not the whole hard disk. |

 |
DriveCrypt Key Features:
1. Strong Cryptography
2. Easy to Install, Deploy & Use
3. Maximize Your Security, Minimize Your Risk
4. Disk Partition and file volume encryption
5. Invisible Containers
6. Hide data into music files
7. Easily encrypts Pen-Drives and USB disks on a container or partition level.
8. Improved Password Security
9. Password Sniffing Protection
10. No-Evidence Encryption
11. Administrator Password Control (keyfiles)
12. Anti Dictionary or Brute Force Attack mechanism
13. Easy and fast hotkey control
14. Second User Access
15. Forgotten user password recovery
16. Eliminate the Danger Of Unattended Computers
17. Secure Disk Deletion (Disk Wiping)
18. Encrypted Volume Resizing
19. External Hardware Support
20. Works on any Storage Medium
21. Installation is Easy and Safe
22. Encrypted Data is Easily Recovered
23. No Backdoors present
1344 Bit Military Strength disk encryption using the best and most proven cryptographic algorithms such as AES, Blowfish, Tea 16, Tea 32, Des, Triple Des, Misty 1 and Square.
2. Easy to Install, Deploy & Use
DRIVECRYPT data encryption software requires minimal administration and user training. Disk encryption is completely transparent, requiring no change in the way users work with the computer.
3. Maximize Your Security, Minimize Your Risk
DRIVECRYPT protects your data with very fast and a true "on the fly" disk encryption process. Other products that claim to be "on the fly" decrypt an entire file and load it into memory, creating significant security risks. DriveCrypt file encryption software is smarter and more secure because it decrypts only the specific portion of a file that is in use. Unprotected data never resides on a DriveCrypt encrypted hard drive.
4. Disk Partition and file volume encryption
(Partition encryption with DriveCrypt standard edition only)
DRIVECRYPT allows both, the encryption of an entire Hard Disk partition, as well as the creation of a virtual container file that will store all the encrypted information.
DRIVECRYPT allows both, the encryption of an entire Hard Disk partition, as well as the creation of a virtual container file that will store all the encrypted information.
5. Invisible Containers
(DriveCrypt standard edition only)
The DriveCrypt Standard Edition has the ability to create an INVISIBLE disk INSIDE a container or partition. This way you define two passwords for a container. The invisible disks password gives you access to your working disk, which is hidden in the unused area of your "outer" disk, while another password gives you access to the pre-setup DriveCrypt volume in which you only store data that you would want others to believe is the only data in the container or partition. This is very useful in cases where an aggressor may force you to reveal the DriveCrypt disk's password: By revealing the password of the first or "outer" disk, the aggressor will ONLY see the "prepared data": IE data you put in there, before creating the hidden disk, while he will not be able to see or get evidence that there is another invisible container that securely stores confidential data on the disk.
The DriveCrypt Standard Edition has the ability to create an INVISIBLE disk INSIDE a container or partition. This way you define two passwords for a container. The invisible disks password gives you access to your working disk, which is hidden in the unused area of your "outer" disk, while another password gives you access to the pre-setup DriveCrypt volume in which you only store data that you would want others to believe is the only data in the container or partition. This is very useful in cases where an aggressor may force you to reveal the DriveCrypt disk's password: By revealing the password of the first or "outer" disk, the aggressor will ONLY see the "prepared data": IE data you put in there, before creating the hidden disk, while he will not be able to see or get evidence that there is another invisible container that securely stores confidential data on the disk.
6. Hide data into music files
Using special so called "Steganographic" functionalities, DRIVECRYPT allows you to hide all your sensitive information into music files. Just authorized users will be able to access secret information, anyone else will only find harmless music on the computer…
7. Easily encrypts Pen-Drives and USB disks on a container or partition level.
With the HOT Disk option, DriveCrypt can also optionally automatically request the users authentication data as soon as the USB device is inserted. When the USB disk is removed from the computer, all the data are automatically inaccessible to unauthorized persons.
8. Improved Password Security
DRIVECRYPT allows administrators to configure several password settings:
- Master Password Settings
- Restricted second user Passwords
- Second user Password Expiration
- Console Lock-Out Password
9. Password Sniffing Protection
DRIVECRYPT integrates special functionalities that prevent passwords from being sniffed by Hackers or Trojan horses such as Back Orifice, SubSeven etc...
10. No-Evidence Encryption
DRIVECRYPT container files do not have any file header that indicates it is a DriveCrypt encrypted file. Therefore, without knowing the right passphrase, it is impossible to prove that a large container file on the computer is a DriveCrypt virtual disk container.
11. Administrator Password Control (keyfiles)
DRIVECRYPT allows system Administrators to assign different passwords to different users.
12. Anti Dictionary or Brute Force Attack mechanism
DRIVECRYPT makes Dictionary or Brute Force attacks against encrypted volumes much harder than any of the actual competitor products by dramatically slowing down these processes.
13. Easy and fast hotkey control
DRIVECRYPT allows the most used commands like mount or dismount encrypted volumes… to be rapidly accessed trough Hotkeys and/or the toolbar.
14. Second User Access
DRIVECRYPT allows the creation of a master password, as well as different lower rights second user passwords (keyfiles).
15. Forgotten user password recovery
DRIVECRYPT allows administrators using the master password, to access an encrypted disk even if the user has forgotten his user password. This ensures that a company can restore a user password if forgotten. DriveCrypt prevents loss of valuable data from user's workstations and notebooks by allowing three methods of encrypted data access: the Master Password, the user password (keyfile) and/or hardware device access such as optional fingerprint-/Smartcard Readers or USB Token devices.
16. Eliminate the Danger Of Unattended Computers
DRIVECRYPT provides an automatic and/or manual lock-out feature that locks out the user's console and displays a password-protected screen saver. This lock-out functionality can be activated manually or automatically after a specified period of computer inactivity. The computer remains secure even when left unattended. To restore the screen and unlock the keyboard, the password for the current user or Master Password must be entered.
17. Secure Disk Deletion (Disk Wiping)
DRIVECRYPT allows you to wipe the free space on a disk.
This ensures that deleted files will never be recovered by special disk tools.
18. Encrypted Volume Resizing
(DriveCrypt Standard edition)
An Encrypted Volume may, with time, become too small or too big, for the amount of data it has to contain. Therefore, DriveCrypt offers you a Volume-Resize functionality. This will allow you to easily adapt a volume to your needs at any time, and optimise the Hard Disk space.
An Encrypted Volume may, with time, become too small or too big, for the amount of data it has to contain. Therefore, DriveCrypt offers you a Volume-Resize functionality. This will allow you to easily adapt a volume to your needs at any time, and optimise the Hard Disk space.
19. External Hardware Support
DRIVECRYPT supports optional external hardware devices such as: Fingerprint and Smartcard reader, as well as USB token.
20. Works on any Storage Medium
DRIVECRYPT works on any kind of Hard Disk, and removable medium such as Floppy-, Zip-, Jazz-, Sygate-, CD-Rom, DVD- Drives etc… and manages up to 16 TERABITE of encrypted data (Standard edition) or 4 GB (Home Edition)
21. Installation is Easy and Safe
The installation is easy and fast. During installation, the administrator simply selects the drives to be encrypted, the encryption method he would like to use and the master password. DRIVECRYPT will then make the rest and crypt the selected disks.
22. Encrypted Data is Easily Recovered
If a user leaves the organization, the encrypted data on the PC is easily recovered and restored to a decrypted state by the administrator using the Master Password or the Local Administrator Password.
23. No Backdoors present
DriveCrypt does NOT include any backdoor. Encrypted data are only accessible by the legitimate users. Neither the vendor nor any other entities are able to break DriveCrypt disk encryption.
*We recommend customers purchase the 12 months assistance, upgrade and online-support @ 30% of the list price.
Full disk encryption with pre-boot authentication
Ideal to encrypt an entire computer /notebook/ partition or just a single Hard drive. With DCPP the Hard drive (including the operating system) is encrypted 100%, therefore unauthorized person will not be able to see even temporary files, installs software etc. DriveCrypt also allows to create a hidden operating system: By entering the correct password, the disks are open, if however you are forced to reveal a password, you could reveal a pre-configured “fake” password and the disk will open showing fake, prepared information.
DriveCrypt Plus Pack - Full Disk Encryption
- Full Disk Encryption (Encrypts parts or 100% of your HardDisk)
- Pre-Boot authentication
- Allows secure hiding of an operating system inside the free space of another OS.
- Strong 256bit AES encryption
- USB-Token authentication at pre-boot level
DriveCrypt Plus Pack
DriveCrypt Plus Packprovides true real-time "on the fly" 256-bit disk encryption. Providing advanced FDE (Full disk encryption) as opposed to VDE (Virtual disk encryption) or "container" encryption, DCPP is an important evolutionary step in the field of transparent data protection.
DCPP
DCPPallows you to secure your disk(s) (including removable media) with a powerful and proven encryption algorithm (AES-256) at the sector level, ensuring that only authorized users may access it. The encryption algorithm used by DCPP is a trusted, validated algorithm chosen by the National Institute of Standards and Technology (NIST) and stated to be the cryptographic standard for years to come. AES-256 is a FIPS-approved symmetric encryption algorithm that may be used by U.S. Government organizations (and others) to protect sensitive information.
DCPP file encryption software is automatic and completely transparent to the user. Not only does this decrease user involvement and training requirements, but also it creates the foundation for enforceable security. The careful integration of boot protection and automatic encryption provides a high degree of security with minimal impact on users. Boot protection prevents subversion of the operating system (via floppy boot-up, for example) or the introduction of rogue programs while sector by sector encryption makes it impossible to copy individual files for brute force attacks. DCPP Windows encryption safeguards the operating system and the important system files (which often contain clues to passwords for Windows).
DCPP is the fastest and most feature-rich real-time full disk encryption system available, Special care has been taken to render all cryptographic parts as invisible & transparent as possible.
DCPP file encryption software is automatic and completely transparent to the user. Not only does this decrease user involvement and training requirements, but also it creates the foundation for enforceable security. The careful integration of boot protection and automatic encryption provides a high degree of security with minimal impact on users. Boot protection prevents subversion of the operating system (via floppy boot-up, for example) or the introduction of rogue programs while sector by sector encryption makes it impossible to copy individual files for brute force attacks. DCPP Windows encryption safeguards the operating system and the important system files (which often contain clues to passwords for Windows).
DCPP is the fastest and most feature-rich real-time full disk encryption system available, Special care has been taken to render all cryptographic parts as invisible & transparent as possible.
Pre-Boot Authentication
The user is authenticated by means of pre-boot authentication (PBA) before the system is started and therefore before the operating system is booted. This kind of authentication cannot be manipulated, PBA therefore guarantees maximum security. Neither keys nor passwords are stored on the PC's hard disk. All of the information required to boot the operating system is derived from the password. This makes the use of hard disk tools for analysing the hard disk completely ineffective. PBA in provided by a system call BootAuth and is a fully graphical login screen.
Full disk Encryption
Automatic & transparent Full disk encryption (FDE) offers several key advantages relative to file encryption. FDE secures the system and temp files that often contain sensitive data but are missed by file encryption. Even removing the drive itself does not give access to any file or directory structure. FDE is performed sector by sector without creating temp or backup files. As a result, large files will decrypt without delay whereas file encryption is normally much slower. Whole disk encryption also avoids such time consuming tasks as secure deletes of temp files or work files in clear text, and obviates the need to do a full delete on disks to be discarded.
How does it work?
As data is read from the hard disk, DCPP automatically decrypts the data before it is loaded into memory. When data is written back to the hard disk, it is automatically re-encrypted. This process is completely transparent to the user or any application programs, the data is caught "on the fly" as it transfers back and forth between the hard disk and memory. Consequently, users don't need to remember to decrypt or re-encrypt their data, or change the normal operation of their PC. In addition, only individual sectors are decrypted at any one time, not the whole hard disk. Other products that claim to be "on the fly" decrypt an entire file and load it into memory, creating significant security risks. DCPP is smarter and more secure because it decrypts only the specific sectors of a file that are in use. Unprotected data never resides on a DCPP encrypted disk.
Hidden Operating System:
DCPP is the only disk encryption software on the market able to hide an entire operating system inside the free disk space of another operating system. You can practically define two passwords for your DCPP encrypted disk: One password is for the visible operating system, the other for the invisible one. The first "fake" password gives you access to a pre-configured operating system (outer OS), while the other gives you access to your real working operating system. This functionality is extremely useful if you fear that someone may force you to provide the DCPP password; in this case, you simply give away the first (fake) password so that your attacker will be able to boot your system, but only see the prepared information that you want him to find. The attacker will not be able to see any confidential and personal data and he will also not be able to understand that the machine is storing one more hidden operating system. On the other hand, if you enter your private password (for the invisible disk), your system will boot a different operating system (your working system) giving you the access to all your confidential data. The creation of a hidden operating system is not obligatory and as such, it is not possible for anyone who does not have the hidden OS password to know or find out if a hidden operating system exists or not.
Features and Benefits
Some of the main features & benefits:
- Boot protection
- Pre-Boot authentication: Login before starting the operating system
- Multiple OS boot support (Microsoft)
- Invisible operating system (allows hiding the entire operating system
- Full or partial hard disk encryption
- Sector level protection
- Complete "power off" protection i.e. unauthorised can not boot up the PC
- AES 256 bit encryption
- No size limitation for encrypted disks
- Manages an unlimited amount of encrypted disks simultaneously
- Allows steganography to hide data into pictures
- Trojan and keyboard sniffer protection preventing passwords from being captured
- Anti dictionary and brute-force attack logic
- Encrypts almost any kind of media (hard disks, floppy disks, ZIP, JAZ, etc...)
- Administrator / user specific rights
- USB-Token authentication at pre-boot level (Aladdin R2 and Rainbow USB-Token)
- Facility to validate the integrity of the encryption method
- Recovery disk for "disaster recovery"
- Easy to install, deploy and use
- Completely transparent to the user
- Minimal administration and user training
System Requirements:
*DCPP currently works on Windows NT /2000 /2003 /XP and Vista 32 bit (client and server versions)
Here is a short comparison table between DriveCrypt and DriveCrypt Pack.
*Note that if needed, it is possible to install both products on the same computer
*Note that if needed, it is possible to install both products on the same computer
DriveCrypt |
DriveCrypt Plus Pack |
PocketCrypt |
|
Compatible 2000/XP/Vista |
Yes |
Yes |
Yes |
Compatible Win 98 |
Yes |
No |
Yes |
Compatible Win Mobile |
No |
No |
Yes |
Container based encryption |
Yes |
No |
Yes |
Allows hidden Containers |
Yes |
No |
No |
CD Encryption |
Yes |
No |
No |
Supports external USB token |
Yes |
Yes |
No |
Partition encryption |
Yes |
Yes |
No |
Encrypts entire HD |
Yes, if not boot HD |
Yes |
No |
USB – Stick /disk encryption |
Yes |
Yes |
No |
Allows more then one user |
Yes |
Yes |
No |
Protection of unattended PCs |
Yes |
Yes |
No |
Password sniffer protection |
Yes |
Yes |
No |
Sector based encryption |
Yes |
Yes |
No |
Encrypts operating system |
No |
Yes |
No |
Allows hidden OS |
No |
Yes |
No |
Destruction password (Fake password destroys the disk) |
No |
Yes |
No |
Maximum encryptable data |
16 Terabyte |
Unlimited |
4 GB |
Price |
$ |
$ |
$ |
NOTE:
DCPP Enterprise version available
DriveCrypt Plus Pack is available as Enterprise Version with Management console.
Support:
We recommend our customers and resellers, to purchase 12 months assistance, upgrade and online support.
12 months update, upgrade & online support.
30 % of the list price.
DCPP Enterprise version available
DriveCrypt Plus Pack is available as Enterprise Version with Management console.
Support:
We recommend our customers and resellers, to purchase 12 months assistance, upgrade and online support.
12 months update, upgrade & online support.
30 % of the list price.
DriveCrypt Plus Pack is available as an Enterprise Version offering a Management console. DCPP Enterprise is designed to be very easy to install and use. Distribution of the software and encryption of the client machines is made by the admin through the management console, fully transparent to the user.
SecurStar customers include such notable law enforcement agencies such as Scotland Yard, as well as military and defense departments of several countries such as the Ministry of Defence in Singapore and others, and governmental institutions such as the US Federal Aviation Administration (FAA) .
Actual Customer comments :
- “It was easy to setup and use.”
- ”It enabled us to choose from several “industry standard” encryption algorithms.”
- ”It gave us the ability to transport the executable file from PC to PC.”
- ”When a USB stick is inserted into a USB port a pop up requests a password before access is allowed.”
SecurStar Management Console
|
With an installed platform of worldwide 4.5 million satisfied customers, the products DriveCrypt and DCPP are the worldwide most used disk encryption programs today available on the market.
At high request, SecurStar decided to expand its product portfolio with DCPP Enterprise Edition. This software can manage the installation and administration of the disk encryption software over large networks and allows encrypting desktop and notebook computers quickly and easily. |
 |
DriveCrypt Plus Pack Enterprise Edition
Data are one of the most valuable assets that companies and organizations have.
These assets are in even more danger since "mobile computing" has become a reality: sensitive information is stored on notebooks and removable media.
PCs and mobile devices, with the sensitive and valuable information that is stored on them, are constantly exposed to loss or theft. A company's management team is responsible for taking all appropriate steps to protect a company's data.
Our experienced specialists have elaborated a perfect strategy for your data protection with transparent security that is absolutely easy to use.
DriveCrypt Plus Pack Enterprise is truly user-proof: from the first step of installation till your everyday-work. You don't have to alter your work behavior by being securely protected.
These assets are in even more danger since "mobile computing" has become a reality: sensitive information is stored on notebooks and removable media.
PCs and mobile devices, with the sensitive and valuable information that is stored on them, are constantly exposed to loss or theft. A company's management team is responsible for taking all appropriate steps to protect a company's data.
Our experienced specialists have elaborated a perfect strategy for your data protection with transparent security that is absolutely easy to use.
DriveCrypt Plus Pack Enterprise is truly user-proof: from the first step of installation till your everyday-work. You don't have to alter your work behavior by being securely protected.
· Full disk encryption for Windows
DriveCrypt Plus Pack Enterprise Edition protects your information.
We guarantee easy implementation and enforcement of the IT security policy. The synthesis of boot protection and automatic encryption ensures a high degree of security. FDE encrypts " sector by sector" without generating temporary files and prevents the unauthorized copying of single files.
We guarantee easy implementation and enforcement of the IT security policy. The synthesis of boot protection and automatic encryption ensures a high degree of security. FDE encrypts " sector by sector" without generating temporary files and prevents the unauthorized copying of single files.
· Pre-boot authentication
With DriveCrypt Plus Pack Enterprise Edition the user will be authenticated by pre-boot authentication (PBA) before the system is started and therefore before the operating system is booted. This kind of information cannot be manipulated, because neither keys nor passwords are stored on the hard disk. The start of the system (including booting the operating system) follows after typing in the password.
· Strong 256 bit AES encryption
DriveCrypt Plus Pack Enterprise Edition increases the protection of your data by a strong and tested encryption algorithm (AES 256 bit). Only authorized users have access to your computer. AES 256 bit is an approved symmetric encryption algorithm that is used by U.S. Government organizations (and other)s to protect sensitive data.
· Easy administration through a central administration console
Securstar offers you easy administration from a central console. DriveCrypt Plus Pack Enterprise is also extremely easy to install. The console allows an easy roll-out via network without end-user involvement. You can administrate different PCs and users (import of user managing profile, import or synchronize from the active directory, encrypt or decrypt remote machines …), you have the possibility to group users in a hierarchical structure. Each component can be administrated from a single server. Increase your business and enhance your security.
· Transparent operating and truly user-proof
DriveCrypt Plus Pack Enterprise means easy enforcement of a company-wide security policy. It operates transparently in the background, so end users don't have to undergo training or alter their work behaviours.
· Perfect protection against unauthorized access
DriveCrypt Plus Pack Enterprise is very comfortable. All saved data are encrypted but are visible and accessible for you (after logging in you can access the data). But an unauthorized person can neither log in nor explore your status, the data or its structure.
· Lockout console for unattended computers
DriveCrypt Plus Pack Enterprise offers a special "Lockout Console" function allowing to block the access to the computer, whenever the PC / notebook is unattended. The local console securely hides the screen and only allows people to work after they re-authenticated themselves.
· External media encryption
DriveCrypt Plus Pack Enterprise supports external media encryption (e g Diskettes, ZIP and AZ disks, USB memory sticks).
· Administration of user specific rights
This tool allows the administrator to articulate the rights of every individual user inside the network. Each user gets his level of access, depending on his rights. The user can be restricted in time and also in terms of the value of information.
· Password Policy
DriveCrypt Plus Pack Enterprise Edition offers administrators the possibility to set complex password policy options. Also banned passwords can be specified. This forces users to follow the company guidelines when setting their passwords.
· Password recovery / challenge response
If the user forgets his authentication data, the administrator can reset the password remotely authenticating the user through a challenge response mechanism.
DriveCrypt Plus Pack Enterprise is the first centrally managed encryption software, where its central administration console can install the encryption software directly on the client machine.
DriveCrypt Plus Pack Enterprise is the first centrally managed encryption software, where its central administration console can install the encryption software directly on the client machine.
Another customer requested feature is the “challenge response password recovery”. This allows the centralized recovery of forgotten passwords.
All functionalities have been designed to be extremely intuitive to use and allow companies to encrypt and secure computers quickly and easily.
DriveCrypt Plus Standard Vs. DriveCrypt Plus Enterprise
DriveCrypt Plus Standard:
Full hard disk encryption for single Computers and Notebooks. The administration is done directly on the protected machine. Target group: Home user and companies who need strong full disk encryption, without requiring a centralized installation and configuration console. SecurBoot is also known as DriveCrypt Plus Pack. |
DriveCrypt Plus Enterprise:
Full hard disk encryption with a central management console. The SecurStar enterprise manager allows central installation and configuration over the Network. Target Group: Small and large enterprises with the need of a management console for the automatic, centralized installation and configuration of the software. |
|---|
Encrypts shared hard disks, network disks or folders enabling simultaneous user access. ShareCrypt has been designed to encrypt the shared network drives efficiently and transparently why allowing different users simultaneous data access and prevent unauthorized access from non-authorized people. With ShareCrypt, a certain department could share confidential data, while administrators would not have access to information while still being able to make secu Shared encryption
| ShareCrypt has been designed to effectively and transparently encrypt shared network drives or folders by allowing simultaneous data access to different users and preventing unauthorized access from non-authorized people. |  |
ShareCrypt is very easy to use and it encrypts data with strong encryption algorithms such as AES 256 bit and Blowfish 448 Bit.
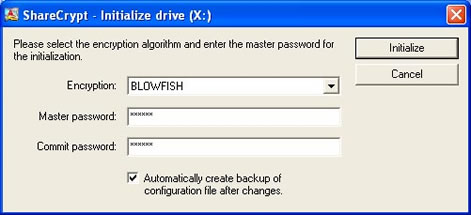
ShareCrypt is a client-based concept: A client user sets an encrypted shared folder/disk and defines other users access level by setting up additional passwords. Everyone with a valid password can read or write data on the encrypted shared disk even simultaneously
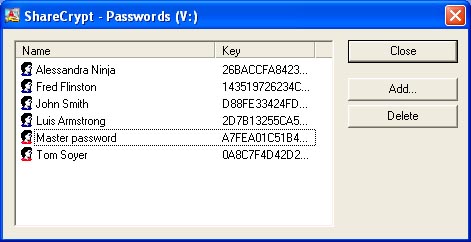
The only thing an administrator has to do is to make an empty shared disk/folder available for read/write access over the network.
ShareCrypt allows an exact division between network administration and administration of sensitive data.
ShareCrypt can prevent administrators to read confidential information they are not supposed to access: All confidential data that client users stores on the shared drive will stay encrypted 100% of the time, therefore if administrators are not authorized to see the data, they will not be able to read any file content, while they will still be able to securely make any kind of security backup (total, incremental, differential, etc...) like if they where backing up any normal (non-encrypted) file/folder.
ShareCrypt does not require any software installation on the fileserver. This way, all CIFS/SMB server systems like MS Windows, Novell Netware 6 and UNIX with Samba are supported.
ShareCrypt is fully scalable and allows the creation and management of an unlimited amount of encrypted disks/folders. (The size of encrypted disks is also unlimited)
ShareCrypt allows an exact division between network administration and administration of sensitive data.
ShareCrypt can prevent administrators to read confidential information they are not supposed to access: All confidential data that client users stores on the shared drive will stay encrypted 100% of the time, therefore if administrators are not authorized to see the data, they will not be able to read any file content, while they will still be able to securely make any kind of security backup (total, incremental, differential, etc...) like if they where backing up any normal (non-encrypted) file/folder.
ShareCrypt does not require any software installation on the fileserver. This way, all CIFS/SMB server systems like MS Windows, Novell Netware 6 and UNIX with Samba are supported.
ShareCrypt is fully scalable and allows the creation and management of an unlimited amount of encrypted disks/folders. (The size of encrypted disks is also unlimited)




